Ten Secrets That Experts Of data centre audit Don't Want You To Know.
Data Center Request for Proposal
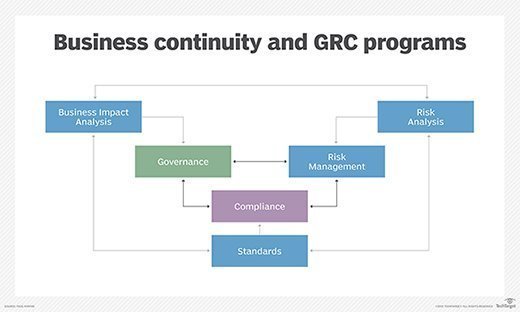
Discover the Modern day Data Center
Whether or not it’s remote hands teams functioning as an extension of a colocation customer’s IT division or data center personnel committed to sustaining the facility’s difficult infrastructure, the human element of information center operations is critically critical. Even though data centers hold the certificates and attestations to demonstrate their compliance with different regulations, basically colocating with them doesn’t take away the burden of compliance from a business. Organizations are still legally accountable for making certain that their operations meet all compliance requirements, which really usually comes down to preserving high levels of information security. As several high-profile situations have shown over the final few years, a information breach can trigger serious financial and reputational harm to a company. There is a wide range of compliance standards organizations want to take into account when evaluating the best options for managing their data.
What is a data center technician?
Nlyte Software is the world's leading software company focused on planning, managing and optimizing data centers. Nlyte's proven platform is used in the data centers of some of the largest and most valued companies in the world.
Based upon the nature of their company, some of these requirements will have higher priority than other people, and some might not even apply to them. A business that handles any type of healthcare data, for instance, demands to locate a HIPAA certified information center that can demonstrate compliance with HIPAA/HITECH regulations, which aid to shield patient privacy. If the company’s principal focus is e-commerce, even so, PCI DSS three.2 compliance, which sets safety standards for protecting economic data during credit card transactions, could be their most critical consideration.
Is Azure a Tier 4 data center?
Tier 1: A Tier 1 data centre has a single path for power and cooling and few, if any, redundant and backup components. Tier 2: A Tier 2 data centre has a single path for power and cooling and some redundant and backup components. It has an expected uptime of 99.741% (22 hours of downtime annually).
Tier 4 is developed to host mission essential servers and computer systems, with totally redundant subsystems (cooling, energy, network hyperlinks, storage and so forth) and compartmentalized security zones controlled by biometric access controls approaches. Naturally, the simplest is a Tier 1 data center employed by tiny organization or shops. Simply because of their higher concentrations of servers, often stacked in racks that are placed in rows, information centers are occasionally referred to a server farms. They offer important services such as information storage, backup and recovery, information management and networking.
Complicated acronyms aside, the SSAE 16 is not something a company can obtain. It is an attestation regular employed to give credibility to organizational processes. As explained above, it is important to conduct a risk assessment and implement proper security controls in order to achieve compliance to ISO 27001, making sure a secure Information Center.
The IT infrastructure of any organization is mainly dependent on the hardware (like servers, storage, and so forth.) which is in the Data Center. This implies that, whenever an organization implements ISO or other details security requirements, the organization wants to take into account the above-described risk assessment for the Information Center to totally defend the data. Network safety is very challenging to handle as there are multiple methods to compromise the network of an organization.
Sort I reports are dates that contain a description of the data center’s systems and the tests they use to decide regardless of whether their controls are developed appropriately. Variety II reports, include a description of the information center’s method and test the style and operating effectiveness over a period of time it relocation (normally 12 months). Most executives will agree, keeping their data safe while still getting access to it is a concern when looking at third-celebration data centers. With data center security and handle as best priorities, here are five variables to add to your data center checklist when choosing a data center provider. Even if a information center has all the gear and processes in location to deliver high-functionality solutions, those sources will go to waste without having an effective operations team in spot to handle that infrastructure.
HIPAA compliance is mandatory for healthcare organizations and vendors like information centers. Hosting providers should meet HIPAA compliance requirements to defend confidential information that comes below their care. An independent auditor can support establish no matter whether the data center is following the appropriate policies and procedures set forth to provide HIPAA-compliant hosting options. If you're in the information center, mission vital or cloud services industries, or you sell to the data center industry, do not miss our weekly update newsletter -- Data Center Sales & Marketing Institute (DCSMI) Update Newsletter. Constantly monitoring essential facilities infrastructure, DCIM software program polls equipment, collects, trends, and reports on data, and monitors for threshold violations.
Also, with increasing popularity of teleworking, there is a risk of virtual attacks. For more about teleworking, please study the write-up How to apply info safety controls in teleworking according to ISO 27001. A Information Center is basically a constructing or a committed space which hosts all vital systems or Info Technologies infrastructure of an organization. The quantity of security attacks, which includes those affecting Data Centers are rising day by day.

- Both are big, effectively-secured facilities constructed to property complex and expensive IT infrastructure that demand sophisticated power and cooling systems.
- The SAS 70 certificate is formatted to permit auditors to review the procedures, established by service organizations, referred to as controls on the report.
- Below the law, healthcare providers, plans, and data clearinghouses (referred to as covered entities by HIPAA) had been provided guidelines they had to follow – in which case they would achieve HIPAA compliance and steer clear of violations.
- By actively aggregating best-of-breed cloud firms and investing in folks, tools, and processes, Otava’s international footprint continues to expand.
What is Tier 3 datacenter?
Some of these data centers are truly gargantuan. The world's largest, in terms of available power supply and cooling system capacity, is Switch Communications Group's SuperNAP-7 in Las Vegas, a colocation facility covering 407,000 square feet (37,811 square metres, or 3.78 hectares, or 9.34 acres).
These data centers are managed by a third celebration (or a managed solutions provider) on behalf of a business. Very best practices mean distinct factors to diverse people and organizations.
The largest challenge of network safety is that approaches of hacking or network attacks evolve year right after year. For example, a hacker may possibly make a decision to use a malware, or malicious software, to bypass the a variety of firewalls and acquire access to the organization’s crucial information. Old systems might place security at risk due to the fact they do not include modern methods of information safety.
With built in alerting, you can react just before failures impact users and services. Data centers include physical or virtual servers that are connected internally and externally via networking and communication gear to retailer, transfer and access digital info. Each server has a processor, storage space and memory, equivalent to a personal laptop but with far more power. Information centers use application to cluster the servers and distribute the workload amongst them.
What is DCIM software?
For the sake of argument, we can start with a figure of $1,000 per square foot. A 1,000 square ft. data center would then cost $1 million, on that basis. A data center of the size that Facebook or Google might use would cost from $250 million to $500 million.
The service delivery and info technology and communications infrastructure sections of the ITIL apply to information centers in distinct. Due to the fact ITIL holds business-standard checklists and procedures, following them will assure that your information center is keeping compliance with these requirements. The Defense Contract Management Agency offers contract administration solutions for the Division of Defense, other federal organizations and international partners, and is an crucial part of the acquisition method from pre-award to sustainment. Decommissioning your servers, HDDs, SSDs and other IT assets just before they leave your information center can be a difficult approach since of the sensitive details they hold. Compliance regulations put restraint on your decommissioning approach too, and it’s crucial to ensure your data center remains efficient, to look following your bottom line.


Information Centers contain all the crucial details of organizations consequently, details safety is a matter of concern. A Data Center have to maintain high requirements for assuring the confidentiality, integrity and availability of its hosted IT (Info Technologies) environment.
This series of articles will concentrate on the major ideal practices applicable across all varieties of information centers, which includes enterprise, colocation, and net facilities. We will go over best practices with respect to facility conceptual style, space arranging, developing construction, and physical safety, as well as mechanical, electrical, plumbing, and fire protection. Facility operations, maintenance, and procedures will be the final topics for the series.
It requires service providers to report on all the specifics concerning their internal access and authorization control practices, as properly as monitoring and notification processes. With these adjustments, the updated standard aims to additional enhance information center monitoring. One particular of the most important precautionary measures against breaches and fraudulent actions, monitoring of vital systems and activities, is a foundation of secure organizations. That might have created a bit much more work for a service provider, but it also takes their safety to the subsequent level.
